Pinterest has taken off like wildfire, reportedly reaching 10 million unique visitors faster than any other website. And on the surface, Pinterest is a blissfully spam free environment. Just lovely pictures.
Nonetheless, the spammers have moved into Pinterest big time. And users are starting to notice.
The first generation of spam involves the spammer posting hundreds of items that go to a spammer’s page which offers an item for sale. When the user clicks to order, it takes them to Amazon for purchase, and the spammer picks up an affiliate payment for bringing the buyer in. This kind of spam has gotten a lot of attention lately.
But there’s novel approach that targets people based upon what they pin.
Let’s say you pin a Gucci purse to your board. You are inadvertently advertising yourself as someone who owns or aspires to own a Gucci purse. And the criminals notice this.
All of a sudden, you pick up a follower like this:
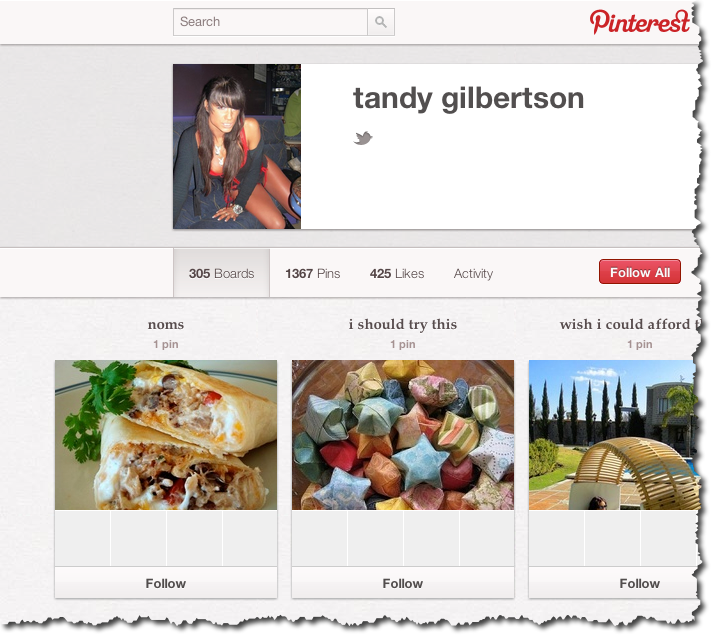
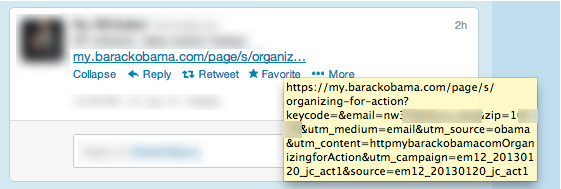
That looks pretty innocent (although Tandy doesn’t say a lot about herself — that’s a tip off). So you think, those star things look good, what are they? You click on the picture and see:
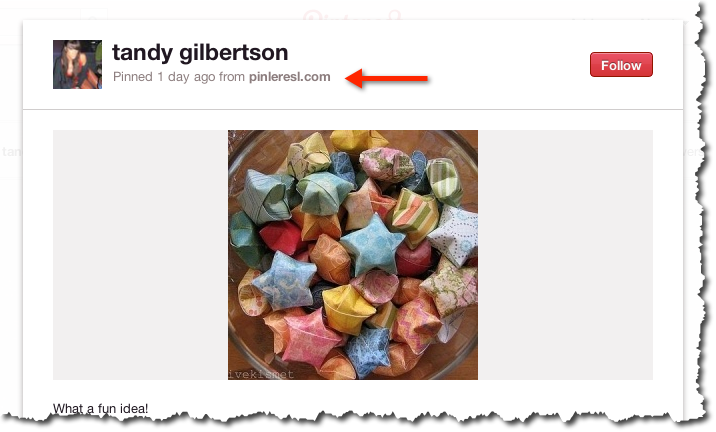
Still not a lot of information. But there’s a clue — I’ve added the red arrow pointing to the tip off that something’s amiss with the page. The URL pinleresl.com is clearly meant to look like pinterest.com.
And so you click the image and are led to a page like this:
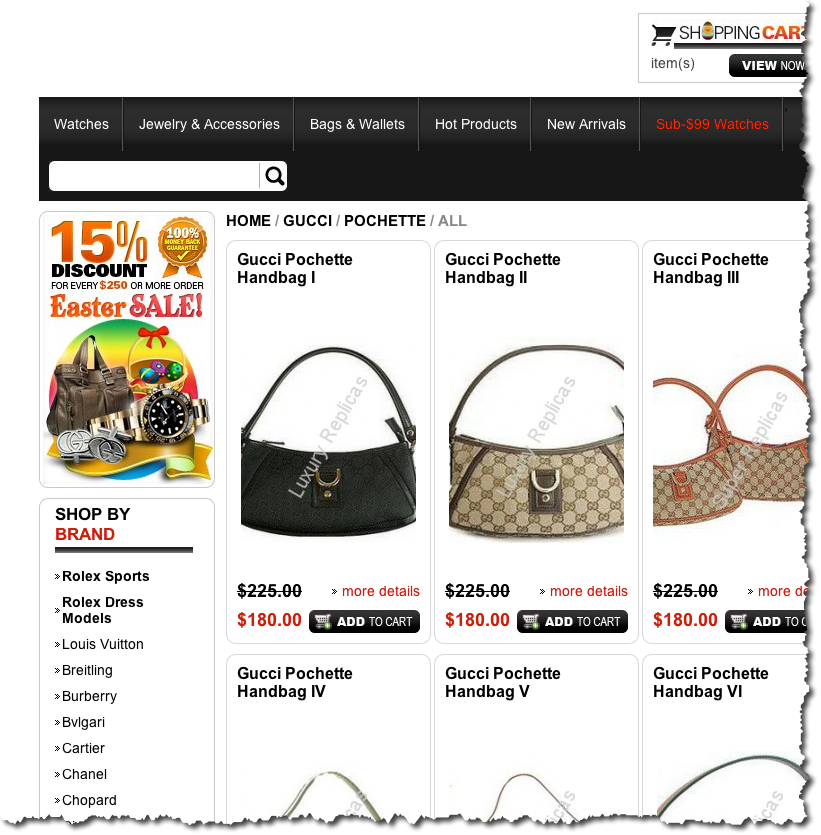
They want to sell you fake Guccis. This is illegal.
A page full of fake Guccis for sale. Why? Because you like luxury purses, and this is targeted to you.
Sometimes the page leads to something that fakes not just the products, but Pinterest’s sponsorship as well:

Click on Image to Enlarge and See the Fake URL
It looks like Pinterest is sponsoring a give-away of L’oreal products — but of course it is not. What is more likely is either that (a) it will try to pry enough personal information out of you to steal your identity or (b) it will try to convince you to install some sort of malware (I played along with one long enough to discover it wanted to install a tool bar in Google Chrome for me), or (c) all of the above. This kind of stuff is bad news if you fall for it.
All the usual scams are out there on Pinterest — phishing, fake contests, malware. Everything on the Internet that is bad is just one click away.
Again, the worrying thing about this is that the spammers aren’t just passively posting catalogs of products they want to sell like has been observed before. They are actively looking for users who express interests in certain brands or products, and targeting with focused content for knock-offs or phishing. You are being targeted by what you pin on Pinterest. This makes it much more likely that you’ll fall for the scam when it is about something you’re interested in.
There are many other examples like this with fictitious Pinterest users whose pins all lead to bad things. Probably nobody knows how much of this is going on, but it is a problem that the brand owners and Pinterest are going to have to grapple with. The availability of spam-bots makes this sort of thing quick and easy to set up.
My wife (the active pinner of the two of us) first alerted me to this problem, and so I sat down and ran through all her followers. I discovered that 50% of her followers are spammers/phishers/pirates. And she’s not unusual. I looked at several of her (real) Pinterest friends and found pretty much that everybody was starting to attract a large collection of spam followers.
What’s especially pernicious is that unknowing Pinterest users are re-pinning spam. Let’s say you see a photo on Pinterest you like. If you don’t click through it, you don’t know where it goes. And so when you re-pin it, all your followers will see it — and if your friends click through (maybe just because you re-pinned it?), they could be infected with a virus because of your repin. Is it your fault? No, you’re a victim too. But it’s insidious how this can spread from user to user like … a virus.
How do you detect it these spammers? Right now, there’s a couple things I see …
- The spammers have lots of boards, but only one pin per board:
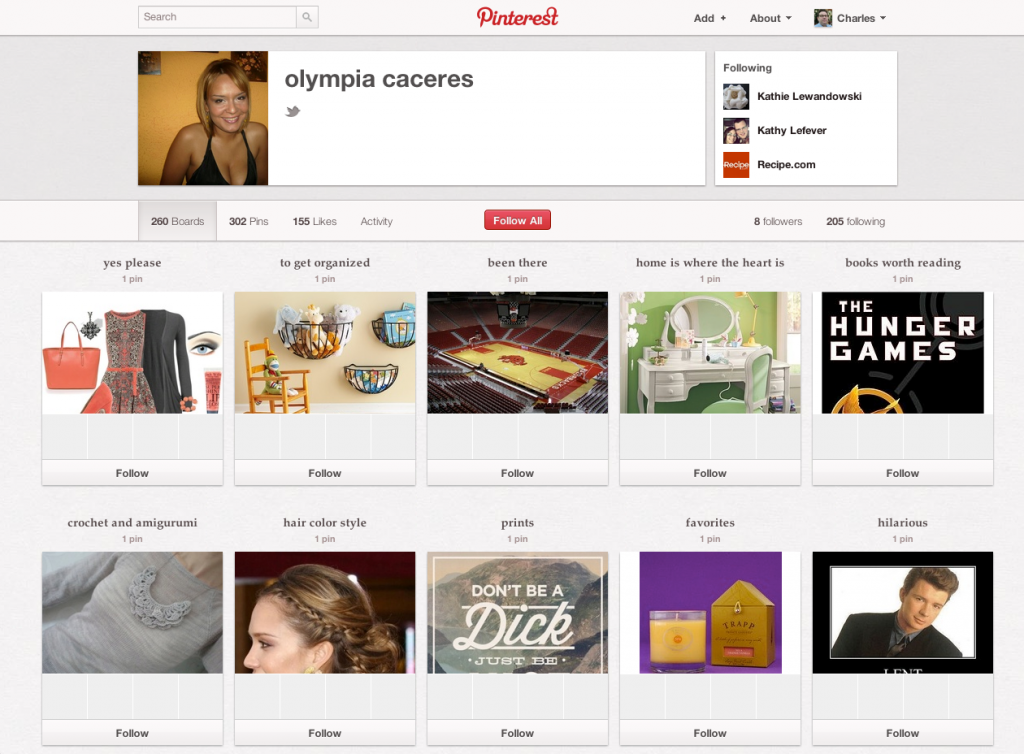
You might have a couple boards with one pin, but every single board with one pin? Not real typical for a Pinterest user. And the description of a lot of these folks is blank. Just a name. So if the user looks unusual — lots of boards, but about the same number of pins as boards — it’s a reason to be suspicious.
- The URLs don’t go to a real web site, they go to a URL shortener like bit.ly or goo.gl:

Not all of these people do this, but if you see a link shortener being used it’s a bright red flag. There’s a fair number of link shorteners out there, but if the web site doesn’t look real to you, it’s worth thinking about. As a note, Pinterest should disallow the use of link shorters like this that hide what the real web site is.
- The URL is trying to fool you by looking like a real site, but is just trying to confuse you — see the second picture in this blog post for the “pinleresl.com” example.
- You click through and see something like this:
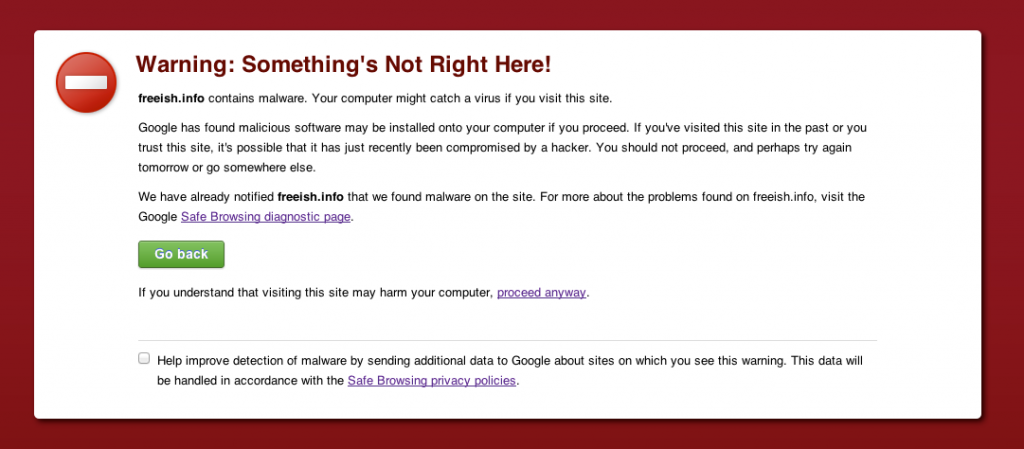
Google says “Stay away!”
You know that’s bad news.
- You see some sort of spoof or phishing site like:
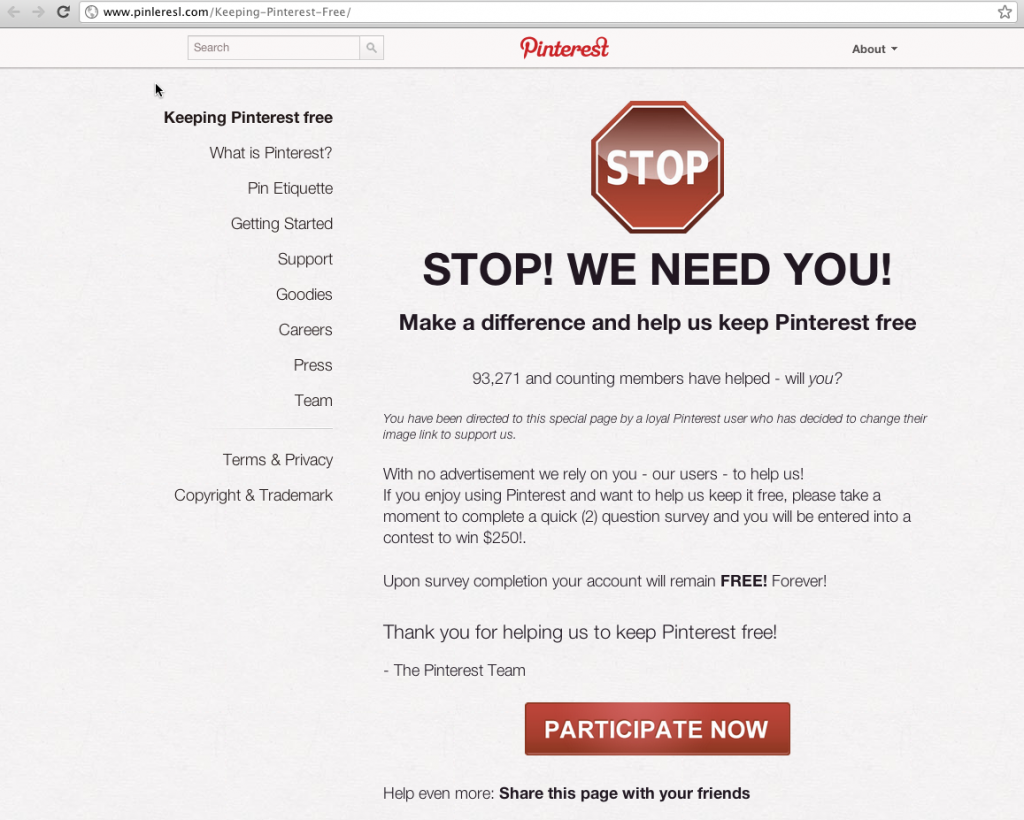
It looks official and real, but it’s totally fake and totally going to rip you off if you “Participate Now”. Again, the URL is the big give-away.
Unfortunately, the problem with giving any specific advice is that the spammers are going to adapt quickly to any patterns we detect. So your best protection is to be wary, know that not everything is as it seems, and if it doesn’t pass the sniff test, get out. If I notice changes in their behavior, I’ll post updates as time goes on. You can follow me on Twitter (socialseercom), sign up for this web site (there’s a link somewhere around here to get notifications of updates), or just check in now and then.
Caveat Pinner — and pass this along to anyone you know who uses Pinterest.
Further reading:
Globe & Mail: Social networking site Pinterest in battle against spammers
Time: Pinterest Easiest Site to Spam Says Man Making $1,000 a Day Doing It