A mystery is happening this weekend. My blog — this blog — normally gets under a hundred visitors a day. Sometimes there’s a burst of activity, frequently tied to the fact that I have a list of all the US Senators’ Twitter accounts — somebody has a hot button issue and tells everyone to come to my site to get their representative’s account. That’s very nice. But this weekend, Google has been visiting a lot. Not declaring itself to be a search engine, mind you, but clearly in an automated fashion thinly disguised as a user. Here’s what I’ve seen:
Category Archives: General
The Top 10 Conservative Hashtags on Twitter (Mid-May, 2014)
Everyone who uses Twitter is familiar with and uses hashtags. But the usage of hashtags is not uniform; some people use them to identify specific topics while others use them as a sort of group identity. For those who use them as group identity, their hashtags tend to stand out in the crowd because of the consistent and widespread usage of them. Topics come and go from day to day, but groups persist. And that gives group hashtags unique staying power.
In the realm of US politics, conservative Twitter users tend to focus on a small set of group hashtags that get high usage as a result. Here are the top conservative hashtags, as a percentage of overall english language tweets:
Does Walmart pay its employees better than left wing magazine “The Nation”?
An email landed in my email box today:
Walmart pays workers 80% more than its liberal critic
Oh, SNAP1! That sounds really bad. Damn liberal hypocrites! A click through to the underlying web site reveals this headline with more details:
Walmart still pays its average associate in N.Y. 80% more than The Nation will be paying its interns.
Hmmm, not quite as bad, but still bad sounding.
The web site goes on to quote an article in The Daily Beast entitled Walmart Calls Out The Nation for Its Low-Wage Internship Program. That article comments on an email sent out by Walmart that chastises The Nation magazine for only now beginning to pay its interns minimum wage (instead of a previous $150 stipend). The Daily Beast article goes on to state that Walmart employees average much higher wages (pointing out an average of $12.53 in Alabama) and get access to health benefits. So “The Nation” is a hypocritical left-wing double-standard holder who demands high wages from Walmart while paying the absolute minimum itself? Let’s look to the evidence presented to support their case.
Twitter Hashtag Spam on #nerdland (Melissa Harris-Perry Show) and What to Do About It
For an update on this topic, please also see my more recent post.
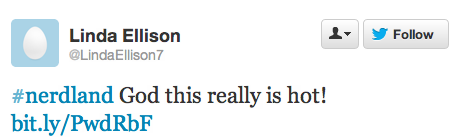
If you like to watch shows such as Up With Chris Hayes or The Melissa Harris-Perry Show and also tweet along with them, you’ve probably been plagued with spam. Whenever a show’s hashtag starts to trend, spammers will begin to swamp the tag with messages like:
What can you do about this?
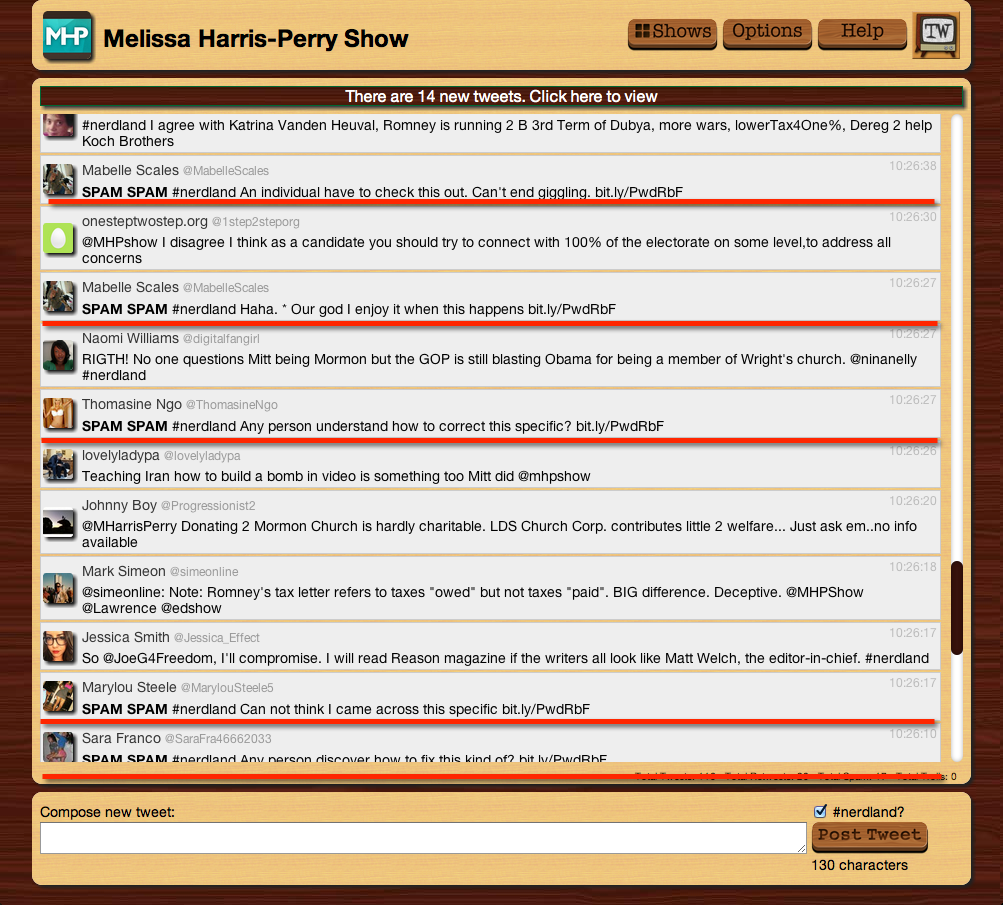
Pretending it doesn’t exist is impossible. During today’s (Saturday 9/22) MHP show, roughly 20% of all Tweets using the #nerdland hashtag were spam. But because the #nerdland hashtag popped in and out of the trending topics list throughout the show, at #nerdland’s peak somewhere between one-third and one-half of all Tweets were spam — and started to crowd out the real tweets.
The normal Twitter spam tools are mostly useless. You could block each user and report them for spamming. But when you see spam messages, on average, every 20 seconds, there is no way to keep up with them. Because the accounts are frequently different, blocking one still allows most of the other spam to show up:
(The SPAM SPAM is not part of the original tweet, but is a flag my Twitter client puts in when it detects spam tweets — see more later in this post).
Clearly, you can try to ignore the spam. It isn’t too hard to identify spam tweets yourself:
- Twitter spam almost always has a URL click. In the case of today’s attack, it ultimately took you to an AOL job listing site where, presumably, the spammer gets paid if you use the site.
- The text of the spam is usually unrelated to the show. And often it’s not particularly gramatical. This is because spammers use sentence generators — one popular one is called “spintext” — that generate sufficiently random sentences to avoid immediate shutdown by Twitter.
A word of warning: you should never click the spammer’s URL. Today’s spam was fairly innocuous, but there are moments like just this week where hackers find a new weakness in a browser and may be able to infect your computer if you visit their web site, even if you have an up-to-date anti-virus and browser. (By the way, there is an update to Internet Explorer just released yesterday, 9/21 — make sure you get it!).
But even if you avoid clicking on spam, you still have the annoyance of seeing it in your Twitter feed. Until Twitter takes it upon itself to stop this, you will need a Twitter client that filters the spam for you. And that’s where I can help you…
The above screen shot is of a Twitter client I built that detects and hides spam (normally, that is: I had it just tag spam tweets with SPAM SPAM for this article). The client is free to use. It does not have advertising that gets in your way. The spam detection is evolving, but it basically looks for patterns in tweets that identify spammers with a very high probability and then prevents the client from showing them to you. It won’t catch the first couple of spam tweets, but after a few of them it detects the pattern and kicks in.
In addition to deflecting spam, the application specially designed for tweeting along with shows like the MHP Show or Up With Chris Hayes. I built it because I am a #nerdland fan and was frustrated with all the other ways to live tweet the show and was annoyed by spam and trolls.
Give it a try, if you like. You can go to its web site at http://www.tweetwatch.tv/, or if you just want to launch the application to give it a whirl, you can start it here: http://apps.tweetwatch.tv/app/index.html. It’s easy to select all the MSNBC shows, as well as all the other cable news shows:
In addition to blocking spam, there are a bunch of other things my Twitter client does to make live tweeting a show more pleasant. It allows you to flag people as “trolls” and hide their tweets (which does not report them to Twitter, as most trolling is not really a violation of Twitter’s terms). It allows you to hide retweets if you wish (you’ve probably already seen the original tweet). And it highlights Twitter users who are connected with the show (e.g., @MHPShow) so it’s easy to spot their tweets in the stream.
I’ll continue to evolve the program to block spammers (as well as other improvements that are unrelated). Give it a try, and give me feedback — my focus is on making it the best possible Twitter client for following along with a show. And if you really hate Danish Modern, I apologize for my theming: I’m also a fan of mid-century modern.
The one paragraph that proves Rick Scott is BSing the DOJ
I am not a lawyer, and so when I looked at the competing letters from the Florida Department of State and the Federal Department of Justice about the voter purge, I thought that, well, it doesn’t look like the law is on the side of Florida — but since our legal code is written in lawyerese and not plain English, I couldn’t be sure what the definition of “is” is in this case.
However, I am a computer systems architect. I work with the largest of corporations on issues of managing their customer data, and the problem of reconciling two lists of customers is a frequent challenge my customers have.
And that is exactly the same problem Rick Scott wants to solve: he wants to match up his list of Florida voters with the list of aliens in the Department of Homeland Security’s SAVE database. Matches would theoretically allow him to identify non-citizens who are registered to vote. Rick Scott points out, correctly as far as I can tell (again, I am not a lawyer), that the law permits Florida to gain access to the database for any lawful purpose. And then he chides the DHS for not fulfilling what he perceives to be their obligations under law.